Create an Azure application to authenticate to Intune Graph module with PowerShell without need to use your own credentials
In this article we will see how to create an Azure app to allow authentication using PowerShell and the Graph API
Context
- You want to use the Microsoft.Graph.Intune PowerShell module
- You want to access Intune resources from PowerShell
- You want to authenticate without having to enter your credentials
Creation of the application
1. Log in to Azure
2. Go to Azure Active Directory
3. Go to App registrations
4. Click on New registration
5. Type a name
6. Choose Accounts in this organizational directory only
7. Choose Client audience
8. In the edit box, enter: urn: ietf: wg: oauth: 2.0: oob
9. Click on Register
10. You now have access to your app info
Creation of the secret client
For authentication we will need a secret.
To create it, you will need to proceed as follows:
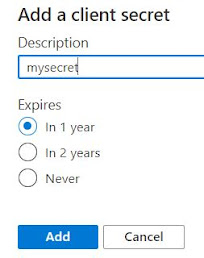
1. Click on Certificates & secrets
2. Click on New client secret
3. Enter a name
4. Choose an expiration time
5. Click Add
6. Your secret client will be displayed
7. Copy it somewhere to reuse it
Authenticate with module
We will now connect to our tenant via the Graph.Intune module and our app.
We will need the following information:
- Name of the tenant
- The client ID of your app
- The secret client
Use the following code to log in:
We will now use a simple cmdlet to see the result.
We want to list the devices: Get-IntuneManagedDevice
We are getting an authorization error.
This is normal because we need to add permissions to our application.
We have to say what this application will do.
Add permissions
First we need to list the permissions we need.
To do this, browse the API doc, link here.
Here the link for the Get DeviceManagement part.
1. Go to your Azure application
2. Click on API permissions
3. Click Add a permission
4. Choose Microsoft Graph
5. Click on Application permissions
6. Navigate to DeviceManagementManagedDevice
7. Check DeviceManagementManagedDevices.ReadWrite.All
8. Click on Add permissions
9. Click on Grant admin consent
10. Click on yes
11. Log in again via powershell
12. Reuse Get-IntuneManagedDevice
13. We now have access























2 commentaires
is the code in this section of the blog missing?
"Use the following code to log in"
It seems to me there is some step that I am missing. I followed exactly as indicated. But a bit confused when I will use the 3 bullet points under Authenticate with module header. Also, Step 11: should I be using connect-msgraph and use my normal creds, or is this where I'm supposed to be using the newly created registered app ID and Value?
Enregistrer un commentaire