Getting started with Logic Apps: Part 5 - Secure MS Graph queries with a user-assigned managed identity
In this post we will see how to secure your Graph API calls by using a user-assigned managed identity.
Welcome in the part 5 of my blog series about Logic Apps.
See below all articles:
In the previous post we have seen how to configure a system-assigned managed identity on a Logic App.
Now let's do the same but using a user-assigned managed identity.
Managed identity
A bit of context
To automate things with Intune, Azure or also on-prem AD you need to authenticate.
As we don't want to set password in plain text in a script or solution we need another way to authenticate.
This is where the managed identity is essential.
But what is it in real life ?
What is it ?
A managed identity is an identity, account in Entra ID.
When you configure a resource to use a managed identity it will create an Azure Enterprise Application.
Your resource (Logic app, Azure Automation) will then authenticate through the managed identity without dealing with credentials.
To enabled a managed identity on a resource, you need to go the Identity part.
You will find there two kinds of managed identity.
Enabling a managed identity to a resource does not allow it to do actions on your tenant, Intune, Azure...
Indeed for this, you need to set permissions on the managed identity.
For instance, to list Intune devices, you need to set at least DeviceManagementManagedDevices.Read.All permission.For instance,
System-assigned
When you configure a system-assigned managed identity to a resource, it creates a new Azure enterprise application.
If you create multiple Logic Apps, for instance, it will create a specific enterprise application for each of them.
A system-assigned managed identity is associated to only one resource.
It also means you need to manage permissions for all of them.
If you have for instance a logic app to manage intune devices, you need to set permissions for device on the managed identity.
If you have another logic app used to manage applications, you need to set permissions for applications on the managed identity.
When you remove a Logic app, the associated managed identity is removed too.
User-assigned
A user-assigned managed identity is an Azure identity that can be associated to multiple resources (Logic App, Azure Automation).
Whereas you can create an system-assigned managed identity by enabling a field on the resource (logic app), with user-assigned, you need to create the managed identity first.
In this post we will configure the logic app to use a user-assigned managed identity.
Create the Logic App
1. Go to Logic Apps
2. Click on Add
3. Choose a subscription
4. Choose a resource group
5. Type a name
6. Choose a Region
7. Select Consumption
8. Click on Review + Create
Create the managed identity
In the previous post, we have seen how to configure a system-assigned managed identity to a Logic App.
We have seen that to do this we can enable to by going to the Identity part.
With user-assigned it's not enough.
Indeed we need first to create the managed identity.
To do this we will proceed as below:
1. Go to the Azure portal
2. Go to Managed identity
3. Click on Create
4. Choose a subscription, resource group, region
5. Type a name
6. Click on Review+Create
Configure the managed identity
1. Go to your Logic Apps
2. Go to Identity
3. Go to the User assigned tab
4. Click on Add
5. Select the managed identity previously created
Note that it can take a while to see the managed identity
6. Click on Add
7. Your Logic app is now configured to use a user-assigned managed identity
Here we configured the logic app to use user-assigned managed identity.
If you go to Enterprise application, you will find an app with the same name than our Logic app.
The app has been created but if we run some Graph API calls with the logic app, it will fail.
That's because we need to add some permissions to the managed identity application.
Set permission
As mentioned above we need to add some permissions to the managed identity application.
It can not be done through the Azure portal but only through PowerShell.
You can find here below a PowerShell that can be used to do this:
You need to configure below variables:
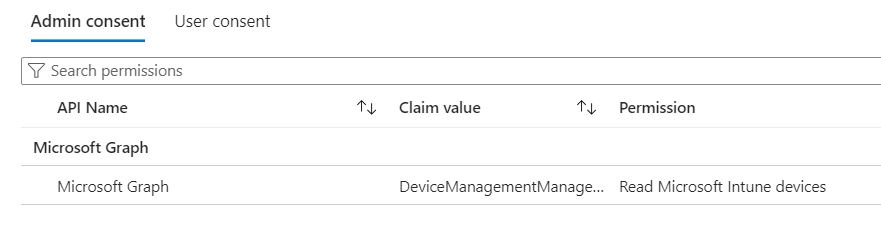
In my case I want to add permission to list Intune devices.
The permission required is: DeviceManagementManagedDevices.Read.All
See below the script to use:
We will then proceed as below:
1. Run the script with with global admin right
2. Go to the enterprise application
3. Go to the enterprise app with the same name then your managed identity
3. Go to Permissions
4. You will find permissions added
Logic App step by step
Step 1 - Recurrence
The Recurrence step in Logic App allows you to schedule the execution of the Logic App.
1. Go to Logic App Designer
2. Click on recurrence
3. Choose your schedule
Step 2 - Query Graph using managed identity
Here we will query MS Graph through the managed identity.
For this, we need to add a new step to do a HTTP request.
In this example we will query devices from Intune with Graph. The appropriate Graph resource to use is: /deviceManagement/managedDevices
We will then proceed as below:
1. Click on New step
2. Choose HTTP
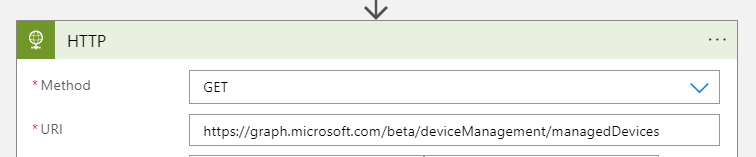
3. In Method select GET
4. In URI type the MS Graph resource URL
5. In our case it's https://graph.microsoft.com/beta/deviceManagement/managedDevices
6. Clic on Add new parameter
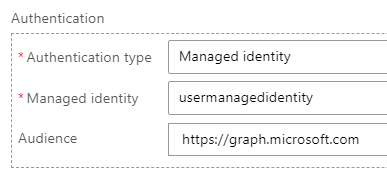
7. Check Authentication
8. Select Managed identity
9. In Managed identity, select the user-assigned managed identity
10. In Audience, type https://graph.microsoft.com
11. Save the app
12. Click on Run trigger > Run
Tadaaa, now you have executed a Graph query using a user-assigned managed identity.





















Enregistrer un commentaire